For our final project in Connected Devices, we were tasked with creating an IoT Thermostat that had a physical UI and temperature sensor built in.
This was achieved using Node and an i2c ADC on a Raspberry Pi W. This was done with lots of amazing example code from Tom Igoe, a few repos in particular:
https://github.com/tigoe/NodeExamples
https://github.com/tigoe/NodeSensorExamples
https://github.com/tigoe/MakingThingsTalk2
Our challenge was to have a device that would post the current temperature to a web server for a week. The twist being that we were going to be under attack by a red team trying to hack our devices.
Check out my code here:
https://github.com/dombarrett/ConnectedDevices2018
The build process was involved but I learned a ton. Constant exposure to Linux command line world is good for me, and I’ll be using these skills frequently in the future. Tying into the physical world was plain ol’ fun.

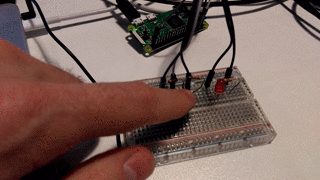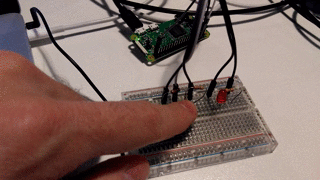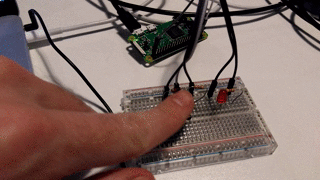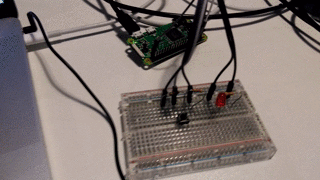
Analog read of the temperature sensor and potentiometer was done by an ADS1015 i2c device. Node has a package for this (common) device called node-ads1x15. Digital in and out for buttons and LEDs was acheived by the onoff node package.
Like so many Linux adventures, this is easier said than done. There were issues installing these libraries, with strange permission errors even when running in sudo mode. There seem to be a couple workarounds, but my most recent and reliable one is using the –unsafe-perm flag on npm installs for these packages.
And having the ADC attempt to read two inputs at once was an issue, which I got around in a seemingly hacky way with only a few errors in my end results.
Then tying in the physical UI to the posting to the web server also took some experimentation. But in the end it worked. I used Amitabh’s guide to setting up UFW on my machine, found here:
https://github.com/tinkrmind/connectedDevices/blob/master/secureYourPi.md
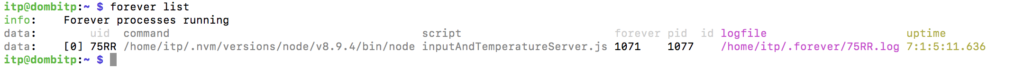
Forever node package was used to keep things running, and Koji was kind enough to help me with a shellscript/cron job configuration to schedule tasks and have activity logs to analyze.
The debrief the following week showed that Amitabh was the only one who was hacked (even though he seemed to recover without noticing). I did not, because I only did UFW and didn’t try to setup a SMPT service to email myself about uptime. That was the attack vector on his machine.
So as far as the NYU network saw, I did not get hacked. However, there seems to be some suspicious activity from my pi on the network. I’ll be digging in deeper to see what might be the case, there.
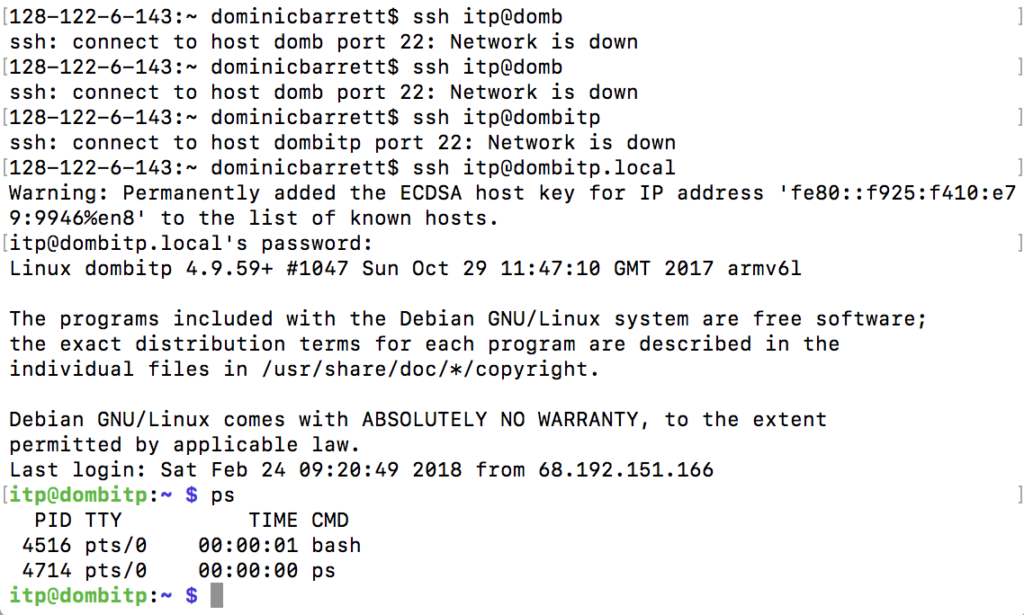
That being said, when I logged into my pi after the exercise, I didn’t see any other processes running:
And it seems like my uptime for my temperature sensor node script was good:
Many thanks to my classmates Koji and Amitabh for all their help.
Really glad to do this exercise, as I’ve already repurposed my setup for my 100 Days project. Amazing how much we can do with such a little, affordable machine.